Expanding the Boundaries of Privacy: Technological Surveillance, Risk Management, and Digital Rights
Introduction: Individual rights and privacy under the tide of The Times
In the past, the Internet era is completely different, and the scope of privacy has become very wide, including all the things we do online, and the flow of data and information generated (Solove, D. 2006). Digital privacy is not only the information we send out, but also the information we collect with various technologies, such as cookies, browser fingerprints, which will record our online behavior.
Back in the 19th century, a Boston lawyer named Warren was so outraged that journalists were gossiping about what his family had for dinner, he teamed up with Brandeis to write The Right to Privacy. Safe to say, he probably never imagined that just over a hundred years later, people would be livestreaming their lunch on social media for the world to see. It’s a wild twist—one that makes us pause and ask: as we enjoy the endless conveniences of the digital age, how much of our personal data is quietly being recorded, stored, and repurposed behind the scenes?

This change makes us have to think about a problem: when people enjoy convenient network services, in fact, personal information is being recorded, stored and used in various ways. Protecting privacy is actually to protect everyone’s right to freedom, and only when a person can decide when, how, and who discloses their information to, can they ensure that they will not be casually disturbed or controlled. Privacy is also related to human dignity, and it is also the basis for trust in the whole society. And important infrastructure. Because new technologies such as cloud computing, big data, and the Internet of Things are increasingly used, the scope of network security protection has expanded from a single computer to a cross-platform, cross-network protection. Companies and governments need to establish a security system from data collection, storage, transmission to processing to prevent data leakage and misuse.

These samples go into storage via process 23andMe calls “biobanking”.https://www.abc.net.au/news/2025-03-25/23andme-bankruptcy-customer-data-saliva-samples-/105092050
There are large number of real examples of data breaches and cyber-attacks. In recent years, a series of data breaches have clearly highlighted the critical importance of cyber security. Genetic testing company 23andMe encountered a security breach that exposed the sensitive health information of millions of users. Because genetic data is difficult to fully anonymize, such a breach can compromise the privacy of individuals, which may also have an impact on their family members, and the case has also contributed to changes in U.S. federal law.
In order to cope with data leakage and network attacks, enterprises and individuals need to take a series of technical measures, the current more common measures include encrypted communication, multi-factor authentication, or the deployment of firewalls, IDS/IPS and other network security tools, relying on these measures to detect and block abnormal access and malicious attacks in a timely manner. These measures have achieved certain influence in the course of practical application.
In addition to technical measures, it is very important to put in place a comprehensive and comprehensive risk management system. Organizations need to develop a data security strategy, clearly define security responsibilities at each step, but also identify specific emergency response processes,
To avoid these risks, companies must conduct security training actions, those international organizations or company must also be set up the information security management system, as is the case of ISO/ ice 27001, the standardization process for data management in security, and under the conditions that there is no risk of data leakage. it is also necessary to take into account third-party security institutions to cooperate regularly security tests as well as a penetration test. This allows for early detection of potential risks. These measures allow companies to maintain effective and continuous protection against the evolution of cyber threats (Siddiqui, S. 2024).
Cybersecurity and data protection are fundamental elements in the digital age. This relies on advanced encryption and defense tools, as well as robust risk management and security strategies for businesses and governments. Only by improving the technical level and the level of management can we effectively prevent security threats such as data leaks and cyber-attacks that have emerged in the era of big data, and provide strong guarantees for privacy and public safety.
In the current development of the digital economy, many large technology companies will collect and analyze huge amounts of user data, gradually developing the so-called “surveillance capitalism” model. This model advertising as sources of profit, also the behavior of users, from individual preferences to negotiation on a same to transform feelings “forecast products, so that users analyze in depth and precise location has become possible, this data collection is omnipresent continuous violation of privacy, and aggravate the inequality in the distribution of power in society, Information resources are increasingly concentrated in the hands of a few giants.

Data enrichment companies build sprawling profiles about millions of individuals. (Getty Images: Malte Mueller)
In some cases, in order to maximize the value of using data, companies and governments most of the time use collect technical user profile composite fragment browser, for example fingerprints, tracking methods, these methods can without the knowledge of the user for data collection and profiles in its smallest detail. Although these techniques can, in some cases, improve safety or personalized service, but the risk of abuse and their personal autonomy that cannot be ignored, regulators must in the development of propulsion technologies and find a balance between the protection of privacy will carefully weigh exactly what are the advantages and disadvantages.
In terms of psychological and behavioral effects, more frequent monitoring can trigger “self-censorship phenomena”. While users aware the final control reports after the completion of the project, when they are deliberately limited to freedom of expression, as well as to express, this would compromise the freedom of expression and innovative thinking, and further undermines trust between peoples in the framework of society and harmony (Warner, M., & Wang, V. 2019).
Evidence of this is the field of education, some schools of artificial intelligence, surveillance software, real-time monitoring of online activities in school equipment, if the initial idea is to prevent violence at school and the risk of suicide, but this monitoring tends to allow students to explore in the expression and their private emotions hesitate, if the situation that lasts for so long, can have a negative impact on students’ mental health and trusting relationships.

Classroom surveillance in schools https://telegra.ph/soundofhope-05-25-402
On the basis of such an analysis, we can conclude that capitalism and surveillance data collection techniques in order to facilitate and social security also has serious violations of privacy and that the power imbalance, how to find a balance between promoting technological innovation and the need to protect individual freedoms, become urgent of the current digital age in the face of legal and political challenges.
The expansion of legal and policy challenges
In today’s digital age, due to the rapid evolution of technology, while data collection methods are constantly being updated, governments of various countries of the world, as well as regulatory agencies have faced challenges that have never been before, the current legal system cannot keep pace with technological advances, this particularly complicates the balance between safeguarding national security, Protection of commercial interests and protection of privacy.
In different countries and regions share their figures as a privacy surveillance regime for the EU, the generic data protection regulation enacted for them imposes on companies with regard to the collection, processing and storage of personal data, there isa need for clear and precise consent of users and the “right to be forgotten” users. Google Spain 2014 is a typical example in this case, the European court of justice ruled in some cases search engines to delete and outdated or inaccurate information, establishing the right to be forgotten ‘legal status this case in order to constantly bring legislation within the EU on data protection, and a huge impact on data governance worldwide.

Ironic graffiti on the street,https://eulawanalysis.blogspot.com/2014/05/the-cjeus-google-spain-judgment-failing.html
In the United States, the conflict between law enforcement agencies and privacy protection is also highly prominent. For instance, in the case of Carpenter v. United States, the police tracked a criminal suspect through mobile phone location data without obtaining a search warrant. Eventually, the Supreme Court of the United States ruled that this practice violated citizens’ reasonable privacy expectations in the digital age. Some people believe that this judgment indicates that although national security is an important goal, the government must strictly follow the legal procedures and restrictions when obtaining personal data. Of course, it is felt that this decision reflects, although national security is an essential objective, but the government’s legal and strictly limited procedures for operations can be consulted On another, from the point of view whether this method can effectively in terms of crime prevention, has helped to reduce the cycle of detection and repression, In cases where use is permitted, should the legal provisions themselves not be changed? Although it might hurts the victims more?In my opinion, the United States is a relatively special country. As a nation where drugs are legalized and there is almost no legal intervention against hate speech, this judgment can only be regarded as a special case of a special country and cannot be generalized.
In addition to the aforementioned situation, the debate over encryption technology has been escalating, and in 2016, Apple’s refusal to help law enforcement unlock the iPhone of a terrorism suspect sparked a heated discussion about the conflict between “back doors” and protecting user privacy. This is not just a matter of corporate technological responsibility, but also raises the bar for legislators to find a balance between national security and civil liberties.
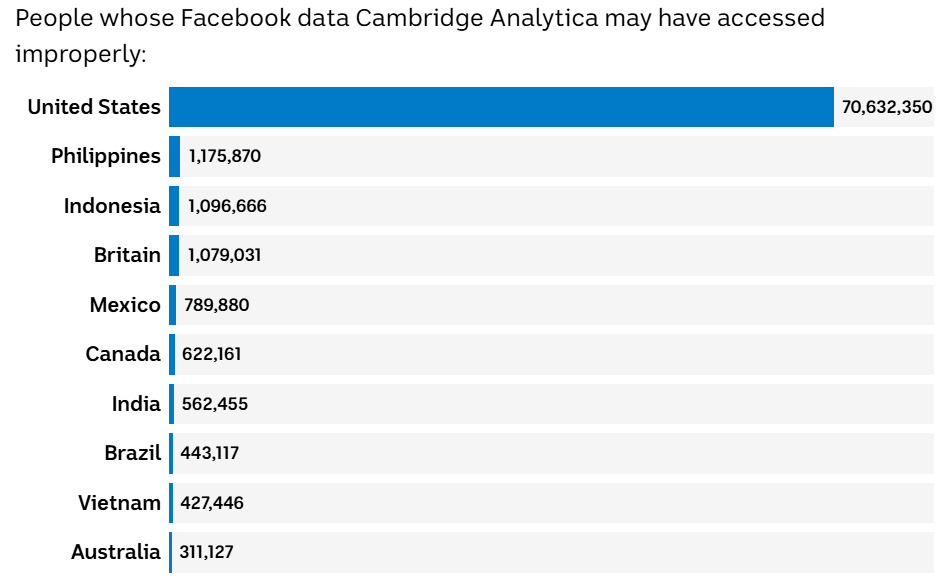
The Facebook entities failed to take reasonable steps to protect those individuals’ personal information from unauthorised disclosure
In recent years, many cases involving corporate data breaches and misuse have received global attention, and the Cambridge Analytica scandal in 2018 is a very landmark event. When it was revealed that Facebook had used the data of millions of users for political AD targeting without fully informing them, European regulators imposed huge fines on Facebook, and the incident led to a global re-examination of rules on data use, This incident clearly highlights the shortcomings of the existing regulatory framework in areas such as cross-border data flows, user consent and data control, and points the way for subsequent revisions to the GDPR.

An estimated 300,000 Australian Facebook users were involved in the data breach. (Reuters: Dado Ruvic)
When faced with emerging technologies such as artificial intelligence monitoring, cross-device tracking, and the Internet of Things, the privacy law now in practice has exposed a lot of problems, and it is very necessary to unify and update legal standards on a global scale, which is also a trend of future development, and some countries are trying to rely on revised legislation to make up for these deficiencies (Suzor, Nicolas P. 2019). The European Union and the United Kingdom have been issuing supplementary guidance documents and updating legal regulations following the revision of GDPR, while the United States is trying to establish stricter data protection regulations at the state level, and emerging concepts in digital privacy such as data portability and the right to be forgotten are driving the international community to redefine individual digital rights. A more uniform, transparent and efficient global data protection framework is likely to be established in the future.
All of these cases suggest that in this digital age, laws and policies can only keep up with the pace of technological development and strike a more reasonable balance between national security, commercial interests, and personal privacy. The outflow of personal data can be restricted, so that data risk management can be implemented at the legal level. It is important, difficult and necessary to protect personal freedom while enjoying the convenience in the digital age. In today’s highly prevalent technological surveillance, how to balance these restrictions and demands will have profound impacts on society and individuals as well as pose severe challenges to legal policies.
Reference
Suzor, Nicolas P. 2019. ‘Who Makes the Rules?’. In Lawless: the secret rules that govern our lives. Cambridge, UK: Cambridge University Press. pp. 10-24.
Solove, D. J. (2006). A taxonomy of privacy. University of Pennsylvania Law Review, 154(3), 477–560.
Siddiqui, S. Y., Farooqi, S., Rehman, W. ur, & Zulfiqar, L. (2024). Human rights for the digital age [Preprint]. arXiv.
Warner, M., & Wang, V. (2019). Self‐censorship in social networking sites (SNSs): Privacy concerns, privacy awareness, perceived vulnerability, and information management. Journal of Information Communication and Ethics in Society. Advance online publication. https://doi.org/10.1108/JICES-07-2018-0060

Be the first to comment