
Introduction
During the era of digital economy, digital assets have become one of the most valuable resources. Personal information—such as gender, age, address, and preferences—has turned into a key source of economic value for businesses. For instance, e-commerce platforms like Amazon use users’ gender, age, and location to recommend suitable products and encourage consumption. Some car manufacturers and real estate companies obtain personal contact information through unknown channels and make unsolicited calls to inquire about consumers’ purchasing intentions and sell houses. Users’ personal privacy and related information are widely used in various fields of the Internet economy. The enterprises gain profits through thousands of hundreds of personal information. At the same time, our personal information is transferred to many people through some unknown ways and becomes more transparent. Inevitably, many lawbreakers steal and sell personal information, which threatens people’s safety in both personal property and physical aspects. Therefore, Why do companies leak customers’ privacy? How should we protect our own privacy and security? By analysing cases involving User privacy leakage, this article aims to find out the conflict between personal data protection and the commercial use of data in the digital age.
Definitions of Privacy, Security, and Digital Rights
Privacy refers to an individual’s right to control their personal information, particularly in terms of collection, storage, processing, and sharing without unauthorized access. It extends beyond data protection to include freedom from excessive surveillance and misuse of personal information (Solove, 2008). Security refers to the measures taken to protect information, systems, and infrastructures from unauthorized access, breaches, alterations, and destruction. It encompasses cybersecurity, data security, and system security, covering encryption, access control, and network defense mechanisms (Schneier, 2015). Digital rights are human rights in the internet era; they include the right to privacy, freedom of expression, access to information, and protection of personal data (Pangrazio & Sefton-Green, 2021).
From these definitions, it is clear that the use of citizens’ or users’ personal information is fundamentally based on consent—in other words, users have the right to upload their data and to decide whether companies or governments use personal information. From this perspective, users have the maximum right to use their personal information. However, the scope of user privacy exploitation is very wide. For example, website search and browsing history can be used for targeted commercial advertising. Phone numbers and addresses provided on different shopping websites can be used to send promotional flyers or product samples. When users authorize and enjoy digital services, they inevitably hand over their information to enterprises for use, making it difficult to effectively protect their privacy rights. The right of privacy should be protected as a guarantor of physical security, liberty of conscience, control over personal space, non-discrimination on the basis of one’s medical condition, sexual orientation, or disability, and freedom from arbitrary intrusion (Flew, 2021).
Real case analysis
Case 1: China CITIC Bank Leaks Customer Privacy Incident
On the afternoon of May 6, 2020, talk show actress Chi Zi posted on Weibo that in an economic dispute with Shanghai Xiaoguo Culture Media Co., Ltd., he found that the company illegally obtained her own CITIC Bank account transaction details as case materials. Then, he issued a cease and desist letter citing infringement of privacy rights. Shanghai Xiao Guo Culture Media Co., Ltd., without his ID card, bank card, or a judicial investigation order, obtained nearly two years’ worth of his bank transaction records. When questioning China CITIC Bank, he was told, “This was done in cooperation with a major client’s request.”
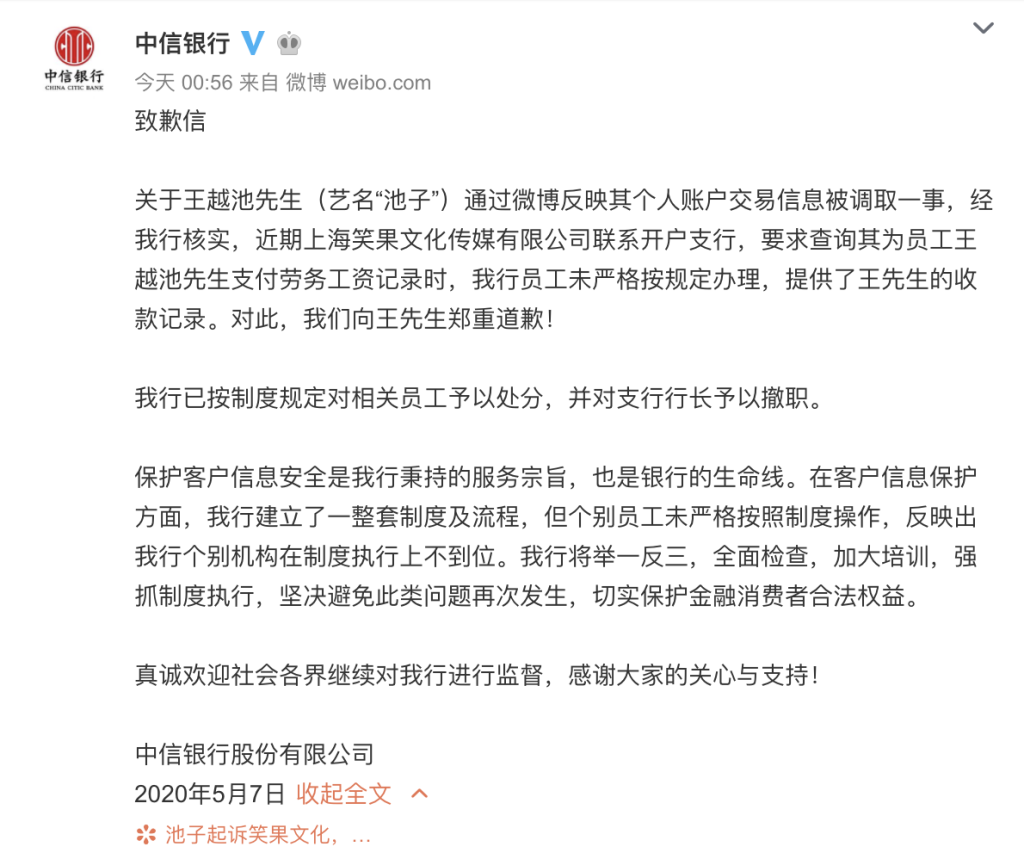
This incident not only reflects the lack of professional ethics among the bank employees involved, but also exposes deep-seated problems in the banking industry. From a legal perspective, China has clearly defined the obligation of financial institutions to protect customer information. The Professional Ethics of Banking Industry Employees (银行业从业人员职业操守) clearly requires employees to “keep confidential the trade secrets of their institutions, protect customer information and privacy”. The Commercial Bank Law of the People’s Republic of China (中华人民共和国商业银行法) also strictly stipulates that “commercial banks have the right to refuse any unit or individual to inquire, freeze, or deduct personal savings deposits, except as otherwise provided by law”. However, the bank employees involved in unauthorized access to and printing of customers’ financial information without their authorization or formal documents issued by legal authorities have constituted a clear illegal act.
More noteworthy is that when there is a conflict of interest between large and small customers, banks tend to sacrifice the rights of small customers to safeguard the interests of large customers. This behavior reflects the abnormal development ecology of the banking industry. Driven by commercial interests, some banking institutions prioritize commercial interests over legal norms and professional ethics. This value orientation issue not only damages the legitimate rights and interests of financial customers, but also erodes the credibility of the entire banking and even financial industry. This phenomenon urgently needs to be highly valued by regulatory authorities.
Therefore, in this industry environment, it is quite difficult for individuals to protect their personal privacy and financial information security. Our accounts and transaction details are held by banks and financial institutions, who have the full right to hand over our personal information to other customers or institutions for profit without our knowledge. Even when the interests of large and small clients conflict, banks exhibit obvious unfair treatment. They prioritize the interests of large customers and arbitrarily trample on the legitimate rights and interests of small customers. So it is difficult to ensure the privacy and financial information security of our individual customers, even small and medium-sized enterprises.
Case 2: Facebook–Cambridge Analytica data scandal in 2018

Cambridge Analytica, a British consulting firm, obtained personal data of millions of users from the social platform Facebook without their authorization and used this data for targeted political advertising. These data were initially collected through a question and answer application called “This Is Your Digital Life”. This application was developed by data scientist Aleksandr Kogan and his company Global Science Research in 2013. Through Facebook’s Open Graph platform, the company not only obtained user data participating in Q&A, but also involved users’ friend information, ultimately collecting approximately 87 million user profiles. Cambridge Analytica subsequently utilized this data for psychological profiling analysis and applied its findings to the 2016 US presidential election, providing data support and strategic recommendations for the campaigns of Ted Cruz and Donald Trump.
After the incident was exposed, Facebook sparked widespread criticism and was accused of serious dereliction of duty in privacy regulation. In 2019, the Federal Trade Commission (FTC) imposed a record breaking $5 billion fine on Facebook; The UK Information Commissioner’s Office also imposed a fine of £500000 on it in the same year. Cambridge Analytica declared bankruptcy in 2018.
This incident has become a privacy scandal of global concern, triggering strong public questioning of social media platforms’ data usage and giving rise to social protest movements such as #DeleteFacebook. More seriously, the incident exposed the fundamental problem of the platform’s business model -sacrificing user privacy for commercial benefits. Most users’ consent is obtained without their knowledge, and lengthy and complex privacy policies exacerbate information asymmetry. Legitimate authorization is not actually based on genuine user informed consent. This reflects that the platform not only failed to effectively protect user privacy, but also abandoned the most basic moral and legal responsibilities, due to commercial interests.
Why do companies leak customers’ privacy?
Business
There is a wide space for utilizing users’ privacy data. Platforms or companies can accurately recommend content which users are interested to them based on their search and browsing history, and use this to determine their purchasing intentions for various products, thereby identifying potential users of goods. In addition, privacy information such as age, gender, and address can also reflect which type of potential consumer the user is, thereby accurately pushing product information and purchase links, and even sending cheap samples to the address for testing. With this recommendation mechanism, enterprises can obtain huge commercial benefits from product companies through advertising, mailing products, and other forms.
User
There is an information gap between enterprises, platforms as well as users. Enterprises or platforms may create convenience for themselves in privacy agreements and other aspects. Due to users agreeing to the agreement by default and not carefully browsing the content, they may allow the company to use personal privacy information without their knowledge. In addition, the users are required to provide personal information as a condition of access to various online products and services (Flew, 2021). For example, some games in China can be registered through authorized WeChat or QQ, so game development companies obtain users’social information and use it to push game advertisements, which poses potential risks. These technology company rationalizes the act of providing privacy, but as the main users, teenagers and young people often lack the cognitive ability to recognize long-term risks.
Regulatory
In many countries, data and privacy protection laws are lagging behind, making it difficult to cope with the rapidly evolving technological ecosystem. In some possible cross-border privacy leakage cases, due to the different scope and authority of privacy protection in different regions, it is not conducive to the handling of related issues, thus allowing companies to disclose user privacy.
The harm of privacy breaches to users

Personal and property safety
Obviously, the transparency of user privacy has allowed many criminals to take advantage of the situation to steal information and threaten the personal safety of users. In reality, there may be stalkers and psychopaths who harass or even track users based on social media positioning and other information, and these victims are mostly women, which has a significant impact on personal safety and physical as well as mental health. Taking the case of China CITIC Bank’s privacy breach as an example, financial institutions such as banks have access to customers’ property information and are highly likely to disclose it to criminals for fraud, posing a threat to users’ property security. If there is a lack of awareness of privacy protection, users are likely to be in danger without knowing it.
User decision-making
User privacy breaches may affect user decision-making. On social media platforms such as Rednote, users choose the category of content they are interested in when they first register, so their personal homepage often pushes content they prefer. Although this meets users’social needs to some extent, it may create an “information cocoon”. Information cocoons refer to the phenomenon where users become trapped in a limited information ecosystem due to algorithmic personalization, leading to reduced exposure to diverse viewpoints and reinforcing existing beliefs (Nguyen et al., 2014). Users may limit their personal thoughts as a result, which is not conducive to expanding their horizons and self-improvement. This invisible manipulation of content damages users’ decision-making autonomy, and platforms often use it to attract advertising investment and earn commercial profits. In addition, on shopping platforms such as Amazon and Taobao, users frequently search for certain types of products and compare prices of different brands in a short period of time. The platform may implement differential pricing based on such behavior, infringing on users’ right to fair trade. Chinese shopping platforms such as Taobao also have a situation where Apple users’ price of products is higher than that of Android users.
How to prevent privacy breaches?
Users
Users should raise their awareness of privacy protection. Firstly, when authorizing platforms or third-party applications, fully read the privacy agreement terms and do not authorize them easily and quickly. Secondly, when sharing own life on social media, do not disclose personal information or casually share location and other content. Thirdly, regularly clean browser and application data to prevent being followed by advertisements or trackers. Fourth, understand relevant laws and policies. If information is leaked, you can file a complaint or report to the relevant authorities.
Enterprise
Firstly, enhance transparency, safeguard users’ right to know about personal privacy usage, and provide the right to delete information. Secondly, eliminate the loopholes in authorization agreements and privacy agreements, and highlight the relevant content. Thirdly, strengthen the supervision of the platforms’ own behavior, eliminate unfair treatment of customers in incidents such as the China CITIC Bank privacy breach, operate with integrity, take protecting customer privacy and property security as the primary responsibility.
The government
Firstly, improve privacy protection laws and relevant regulations. Improve the legal system related to privacy from a global perspective, coordinate standards between different countries. Secondly, strengthen the review mechanism for platform providers and third-party data users. Thirdly, establish a mechanism for reporting and compensating user data abuse. Fourthly, strengthen privacy education for citizens.
Conclusion
In the era of digital economy, platforms and companies often underestimate the importance of privacy protection. As mentioned in the two cases, these companies and institutions prioritize commercial interests and casually disclose users’ privacy, even showing class discrimination, seriously threatening the personal and property safety of users. However, users often unconsciously provide personal information to companies in a passive or active way, lacking awareness of privacy protection. The imperfection of the law and the lack of regulation have further exacerbated this phenomenon. Therefore, only when companies, users and governments trust each other and jointly protect privacy can we create a better Internet environment and promote economic and social development.
Reference
Solove, D. J. (2008). Understanding Privacy. Cambridge: Harvard University Press. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=1127888
Schneier, B. (2015). The Hidden Battles to Collect Your Data and Control Your World. In Data and Goliath. New York: W.W. Norton & Company. Pangrazio, L., & Sefton-Green, J. (2021). Digital rights, digital citizenship and digital literacy: What’s the difference? In New Approaches in Educational Research, 10(1), 15–27. https://doi.org/10.7821/naer.2021.1.616
Flew, T. (2021). Hate speech and online abuse. In Regulating platforms, 91–96. Cambridge: Polity. Protection of Personal Data Rights and Interests. (2020, May 8). The data rights dispute of banks – the commercial interests of large customers and the privacy rights of small customers. https://mp.weixin.qq.com/s/FbWvehtVDspnl0SqH_I2Vw
The Paper. (2020). China CITIC Bank Apology Letter [screenshot]. The Paper. https://m.thepaper.cn/kuaibao_detail.jsp?contid=7287512&from=kuaibao
Wikipedia. (2025, March 9). Facebook–Cambridge Analytica data scandal. https://en.wikipedia.org/wiki/Facebook%E2%80%93Cambridge_Analytica_data_scandal
Trustifi. (2023, May 10). Data leaks: What is data loss prevention? https://trustifi.com/blog/data-leaks-what-is-data-loss-prevention/
Nguyen, T. T., Hui, P.-M., Harper, F. M., Terveen, L., & Konstan, J. A. (2014). Exploring the filter bubble: The effect of using recommender systems on content diversity. Proceedings of the 23rd International Conference on World Wide Web (WWW ’14), 677–686. https://dl.acm.org/doi/10.1145/2566486.2568012

Be the first to comment