
Doxxing: “Your personal information may be publicly revealing without your consent.”
(Source: artist Sergio Ingravalle)
Introduction
In March 2025, a teenager daughter of a Baidu executive easily doxxed and disclosed a pregnant netizen privacy on social media. The incident caused a heated public discussions both in China and overseas. People found that Baidu, known as “Google in China”, and daily social media use have serious risk of leaking personal privacy at any time. The doxxing source “overseas networking database” is involved in a surprising illegal profit chain of personal information trafficking. The key issue of privacy leakage when using digital platforms has also attracted public attention. It is not only individuals who need to pay attention to unintentional privacy exposure in their daily lives, but also the responsibility of governments and platforms to make adequate improvements to reduce negative implications on this critical issue.
A pregnant netizen was doxxed by the teenager daughter of Baidu’s Vice president

Doxxing is a extreme phenomenon in fandom circles
(Source: Fenghuang Weekly)
A user of Chinese social media platform Weibo conducted a doxxing on netizens who disagreed with her comments on a K-pop fan post, and disclosed the netizen’s real name, mobile phone number, home address and other private information to public on her account. Based on the content of the user’s previous posts, other netizens found that the user is the teenage daughter of Baidu Vice President Xie Guangjun, inflaming public attention and anger (Shuang, 2025).
Doxxing is not only illegally collecting personal privacy, but also published the data on the Internet to guide cyber violence, which is a kind of illegal retaliation by invading privacy (Wikipedia, 2025). It may result in the victim facing offline harassment or even criminal threats to personal safety (Hebei Province High People’s Court, 2025). The incident quickly damaged the public trust in Baidu’s capability to protect user data, then Xie Guangjun apologized on social media, but claimed that the information obtained by his daughter came from an “overseas networking database” (Dave, 2025), and Baidu also officially stated their investigation showed it was not from the Baidu database leak. However, people still worry about whether Baidu and social media platforms may has a serious digital security risk of revealing personal privacy, and concern about whether Baidu does not value its users (Zhizu, 2025). At the same time, it also raise public awareness on possible influences of being innocent victimized doxxing victims who just normally blousing various websites in their daily lives.
Digital streaking under the Privacy paradox and inequality
“Your information is exposed at any time when surfing the Internet”

Where can criminals access your personal information
(Source: Namecheap)
Users often let their privacy leak out because of preventing complex steps or negligence. There exists “privacy paradox” in our daily life, that is, people tend to suppose that privacy is an important issue, but in fact, most users often inadvertently or voluntarily disclose their private data information at a very low cost (Gerber et al., 2021). For instance, sharing tasty cuisines on social media platforms, or a photo of your own in a tourist attraction, or post a photo of a warm corner of home. These will be very likely to reveal your location, personal appearance, and home address respectively. Online shopping is also a good case in point. We need to provide our name, phone number and residential address to the shopping platform and merchants. Your life routines can be easily tracked by others in these ways. Are you sure you really care about privacy as you immerse yourself in Posting or shopping on your respective platforms?
Additionally, information inequality existing between the platform and users, which leads to the lack of users independent rights of privacy. Information inequality refers to the situation where users have relatively limited understanding of the platform, while the platform holds a large amount of privacy data related to users (Alex, 2015). Users need to have the right to choose if they want to achieve privacy, but this is difficult to achieve when using applications (Marwick & Boyd, 2019). The way platforms use user data often lacks transparency and reasonable surveillance. Users need to obey the information disclosure and service policy terms of each platform. It is almost impossible for users to read through those Privacy Service Agreements that are dozens of pages long, and there is often a statement that “the platform has the final interpretation right”. Think about it carefully, have you ever paid careful attention to pop-ups that agree to get user information? Have you read through all pages of privacy policies, or have you simply swiped and clicked “allow”? According to Terry Flew (2021), users can easily fall into the trap of “consent fatigue” as platforms obscure their autonomous privacy choices. Many doxxing cases showed that these unintentional dissemination of privacy has become a weapon for malicious use and cyber violence.

Privacy is has been obtained by someone else when clicking “Allow”
(Source:TOPYS)
The astonishing privacy trafficking chain and social implications
Doxxing has revealed serious problems in digital privacy governance, such as unclear gaps of rights and responsibilities, lack of supervision, and even the forming gray profit industrial chains, causing severe negative social impacts. In this digital era, Doxxing is like a unlimited-time bomb of personal privacy. Anyone may become a victim of it.
The girl who disclosed the personal information of the pregnant netizen in the case is just a naive teenager, how could she obtain such information? Some security measures of access and control system on certain platforms are inadequate, or some company partners fail to obey data network security regulations, allowing hackers to obtain real-time user data at any time and subsequently leading to user data leakage (Goggin et al., 2017, p. 9). After that, these data are uploaded to the “Overseas networking database” or sold to some immoral merchants engaged in the grey online industry.After a series of data resales and uploads and AI robot processing, this teenage girl only needs to enter the name or even only the social media ID of the person she needs to dox with super low cost, then she can quickly obtain all the private information related to that person in the “Overseas networking database”. Its detailed level can even include marital status, asset and property status, phone records, etc. The more detailed the contents worth the higher prize. But in other words, one only needs to pay to obtain these information.

The terrifying private information trafficking industry: Your privacy is not valuable
(Source: the RED Note)
On the one hand, this is highly likely to bring endless cyber violence, offline harassment and even criminal activities to the victims, seriously damaging their physical and mental health. Meanwhile, criminals may also use the identity information to sham as victims to carry out illegal activities, directly affecting credit, finances and daily lives of the original privacy owner. On the other hand, these doxxing cases will trigger public anxiety and even social panic over privacy leaks, and the resulting cyber violence is also not conducive to maintaining online privacy and safety. Some professional lawyers have disclosed their comments on social media platforms that most data transactions are conducted through the dark web and overseas platforms, making it difficult to track and effectively govern from the source. What is even more terrifying and ironic is that some of these warm-hearted lawyers have also been doxxed.
How Chinese Doxxing-related Privacy Regulations work and in comparison with Australia
Besides insufficient attention to privacy of users and excessive rights to access user privacy of platforms, there are also weakness in the supervision and protection of laws and regulations. Laws and regulations are the most powerful methods of digital governance, and they will also have their respective direct and indirect impacts on platform measures and user behaviors. The phenomenon of doxxing exists worldwide and always become the focus of public attention because of its serious social impacts. Everyone may become a potential victim and stakeholder. Doxxing cases that occurred this year not only in China, a similar incident also took place in Australia in early April recently, Councillor of Kingston Jane Agirtan was suspected of guiding doxxing to harass a lawyer (Heraldsun, 2025). We can use the relevant privacy laws and regulations of China as an analyzing example and compare the difference and similarities with Australia to find out why the current digital policies related to privacy need to be improved.
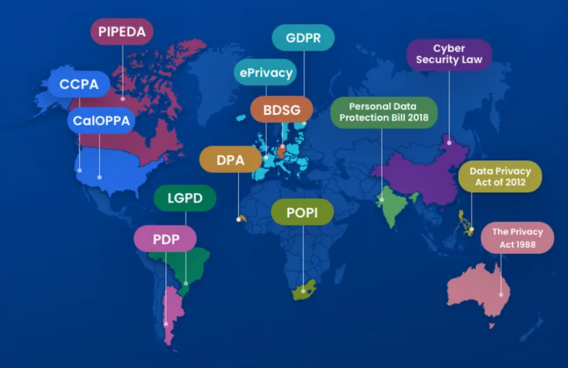
Privacy Laws around the World
(Source: Graphicspedia)
China promote platforms to implement a relatively stricter content review mechanism compared to Western countries, and its overall privacy policy focuses on data protection rather than human rights. The relevant laws related to doxxing include the Personal Information Protection Law (PIPL) and the Civil Code of PRC, in terms of the sanctions for illegal behaviors of personal privacy dissemination and the protection of victims whose reputation rights have been infringed. Its governance has the characteristic of lag than incidents and does not have clearly provision that platforms have the legal obligation to supervise as online discussion environment. This causes many platforms to add some unethical exemption clauses in the user privacy agreement, increasing the difficulty for potential victims to protect their privacy rights. The governance to doxxing incidents mainly depends on self-reporting of the victim and public opinion pressure after the incident to improve. This is one of the main reasons why such behaviors frequently occur on Chinese social media platforms, but they do not always trigger heated public discussions. The case of the teenager daughter a Baidu vice president is considered to be a case that raised serious social impacts among similar kind of cases.
In August 2024, the Chinese government implemented the “Internet violence information governance provisions”, which do not directly stipulate on such incidents. However, it has a certain regulatory effect on the social media cyber violence that doxxing may cause (Zhang, 2024). This is conducive to the platform taking on regulatory responsibilities such as deleting posts for cyber violence caused by doxxing, and it also enables more users to enhance their autonomic supervision and following a healthy online regulation with self-discipline. It is also reflected in this doxxing case. For example, the platform banned the perpetrator’s account more promptly, and most netizens spoke out to condemn the violent teenager doxxing behaviour against the victim, the pregnant netizen. Some netizens even provided some legal assistance and suggestions to the victim.
Compared with China, the online discussing environment in Australia show a higher degree respect for personal freedom of speech and privacy rights, and the legal and regulation system has more detailed and comprehensive regulations and handling methods for privacy violations. Australia’s “Privacy Act 1988”, “Consumer Data Right” (CDR), and Doxxing Prevention Act (2016) have more explicit regulations regarding user rights and platform responsibilities (Corbridge, 2018). Doxxing behavior can be directly prosecuted, fined and held criminally responsible in accordance with the law. The platform also has the relevant legal obligations to delete the relevant contents in-time, even though the Australian Parliament should formulate more detailed reasons for privacy infringement lawsuits to assist doxxing victims (Bei, 2018). In 2024, Australia revised privacy-related acts, made minor updates to the regulations, which further separated and clarified the concepts and differences of doxxing-related crimes among all kinds of privacy violations and crimes, while overall privacy laws still need further improvements (Archbold et al., 2024). Like in the situation of the Australian doxxing case this month, the perpetrator Jane has already lost her parliament member position due to this incident, and she needs to undertake further legal responsibilities.
Privacy governance improvement advice of doxxing

Pay attention to protecting your privacy
(Source: Cyberguy)
For the countries and government agencies related to privacy protection, a targeted legal framework for the doxxing incident is needed. At present, many countries do not pay enough attention to combating doxxing. Comprehensive and separate data privacy laws and regulations are needed to directly prohibit and punish potential doxxing (Kukul, 2023). For example, the Chinese government should enhance the laws and regulations concerning specifically towards doxxing incidents. Once the enforcement and punishment intensity of the laws and regulations for this kind of incidents have increased, the relevant perpetrators will be afraid of the high credit cost and possible results of getting serious punishment, in order to reduce the possibility of similar incidents happening again.
For platforms and application enterprises, more flexible post detection systems and user privacy agreements should be formulated. The companies should strictly abide by relevant laws and regulations, and assume moral responsibilities related to privacy leakage. This is not only beneficial to maintaining the enterprise credit, preventing people from worrying about using products and services of the brand due to similar incidents, but also can maintain a healthy discussion atmosphere and online environment.
Although the government should assume the main responsibility for privacy governance, for individual users, we should always attach importance to managing our own privacy information, since we are the direct subjects related to our own privacy rights. For example, we can regularly clean up the historical privacy information of mobile applications, especially on social platforms, or set the viewing permission for historical published posts. Additionally, users should search and get familiar with the public opinion and reputation of the application regarding privacy before registration. And we need to pay attention to the important terms in the application privacy agreement. Especially, focus on viewing and recording what types of personal information that needs to be authorized on each platform. These can reduce the possibility of privacy such as identity being stolen and misused by potential lawbreakers. If you encounter doxxing situations, collect relevant evidence in-time and make good use of laws and regulations to safeguard your own legitimate rights.
References
Flew, T. (2021) Regulating Platforms. Cambridge: Polity, pp. 72-79.
Gerber, N., Gerber, P., & Volkamer, M. (2018). Explaining the privacy paradox: A systematic review of literature investigating privacy attitude and behavior. Computers & security, 77, 226-261.
Solove, D. J. (2021). The myth of the privacy paradox. George Washington Law Rev., 89, 1.
Marwick, A., & Boyd, D. (2019). ‘Understanding Privacy at the Margins: Introduction’, International Journal of Communication, pp. 1157-1165.
Goggin, G., Vromen, A., Weatherall, K., Martin, F., Webb, A., Sunman, L., Bailo, F. (2017) Executive Summary and Digital Rights: What are they and why do they matter now? In Digital Rights in Australia. Sydney: University of Sydney.
Zhang, R. (2024). The Impact of the “Regulations on the Governance of Online Violence Information” on User Behavior in Chinese Social Media Platforms. Law and Economy, 3(11), 23-27.
Archbold, L., Burdon, M., Cohen, T., & Fraser, H. (2024). Submission to the Legal and Constitutional Affairs Legislation Committee inquiry into the Privacy and Other Legislation Amendment Bill 2024.
Kukul, B. (2023). Personal data and personal safety: re-examining the limits of public data in the context of doxing. International Data Privacy Law, 13(3), 182-193.
Corbridge, Å. (2018). Responding to doxing in Australia: Towards a right to informational self-determination. University of South Australia Law Review.
Bei Li, L. (2018). Data privacy in the cyber age: Recommendations for regulating doxing and swatting. Fed. Comm. LJ, 70, 317.
Shuang Jing (March 20, 2025). Baidu exec’s teen daughter linked to doxing scandal using overseas data in online dispute. TechNode. https://technode.com/2025/03/20/ baidu-execs-teen-daughter-linked-to-doxing-scandal-using-overseas-data-in-online-dispute/
Wikipedia(April 7, 2025). Doxing. Wikipedia. https://en.wikipedia.org/wiki/Doxing
Hebei Province High People’s Court (April 13, 2025). People’s Court News | Open-Box Network Violence Whole-chain Criminal Regulation.Pengpai News. https://www.thepaper.cn/newsDetail_forward_30639987
Dave A. (March 18, 2025). Baidu’s Doxxing Scandal: A Privacy Breach That Sparked Public Outrage! AllAboutAI. https://www.allaboutai.com/ai-news/baidus-doxxing-scandal-a-privacy-breach-that-sparked-public-outrage/.
Zhizu Z. (March 19, 2025). Baidu executive daughter open box incident behind the three warnings. Pengpai News. https://www.thepaper.cn/newsDetail_forward_30438274
Alex Hern (June 15, 2025). I read all the small print on the internet and it made me want to die. The Guardian. https://www.theguardian.com/technology/2015/jun/15/i-read-all-the-small-print-on-the-internet
Heraldsun (April, 2025). Councillor stood down over alleged doxxing shares fresh rant to social media. Heraldsun. https://www.heraldsun.com.au/subscribe/news/1/?sourceCode=HSWEB_WRE170_a&dest=https%3A%2F%2Fwww.heraldsun.com.au%2Fnews%2Fvictoria%2Fsucking-each-other-off-disgraced-kingston-city-councillor-jane-agirtan-goes-on-insta-rant%2Fnews-story%2F9fce3440288d3d76f29317dee0fa57ee&memtype=anonymous&mode=premium&v21=GROUPA-Segment-1-NOSCORE

Be the first to comment